Sit up and pay attention
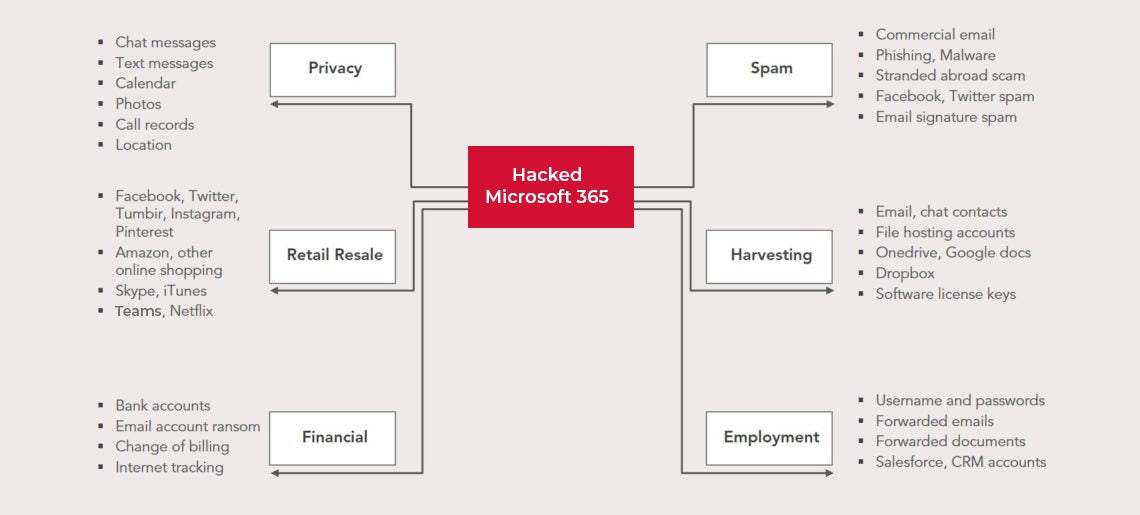
Have you ever sat down and thought about how much the data within your organization is actually worth? First, let’s talk through some facts and figures. Did you know that a truly alarming 85 percent of organizations have suffered email data breaches in the last 12 months? Further, 67% of IT leaders reported an increase in data breaches due to remote work – with the risk being intensified for Microsoft 365 users.
The true value of stolen data
So, what is the motivation behind hackers these days? According to Verizon’s annual data breach report, 86% of all data breaches in 2020 were about money. On average, the cost of a data breach is $4.24M. Insider threats are more damaging, particularly if it’s a compromised account, careless employee misuse, or a malicious insider. The cost of such a data breach could be up to $8.76M.
After a hacker has successfully infiltrated a network and stolen personal data, they’ll often look to sell or even advertise that data on the dark web. No matter the size of your business, the hacker will do everything in their power to demand payment from any customer no matter the size or business sector (charity, health care, or else).
Let’s break down the true value of stolen personal data, item by item:
- Credit card with PIN: $15-$35
- Credit card details: $150-$240
- Stolen online banking logins: $40-$120
- Hacked email accounts (Groups of 2,500+) – $1-$15
- Hacked Social Media Account - $35-$80
- Stolen identity – $0.10-$1.50
- ID/passport scans or templates: $1-$35
- Mobile phone online account: $15-$25
- Full ID packages (name, address, phone, SSN, email, bank account): $30-$100
- Medical notes and prescriptions: $15-$20
- Hotel loyalty from reward program accounts with 100,000 points – $10-20
- Cloud service account – $5-$10
(Sources: Symantec, PrivacyAffairs.com)
Don’t let the numbers fool you: just because they may seem on the lower end of things, you have to consider the size of the data breach itself. Whether a network of hundreds or thousands was compromised, the cost of an attack skyrockets per individual. Hackers today have become more sophisticated than ever, and one user could be the stepping stone to the entire database they’re after. And ultimately, the payout can have a huge and harmful impact on the organization.