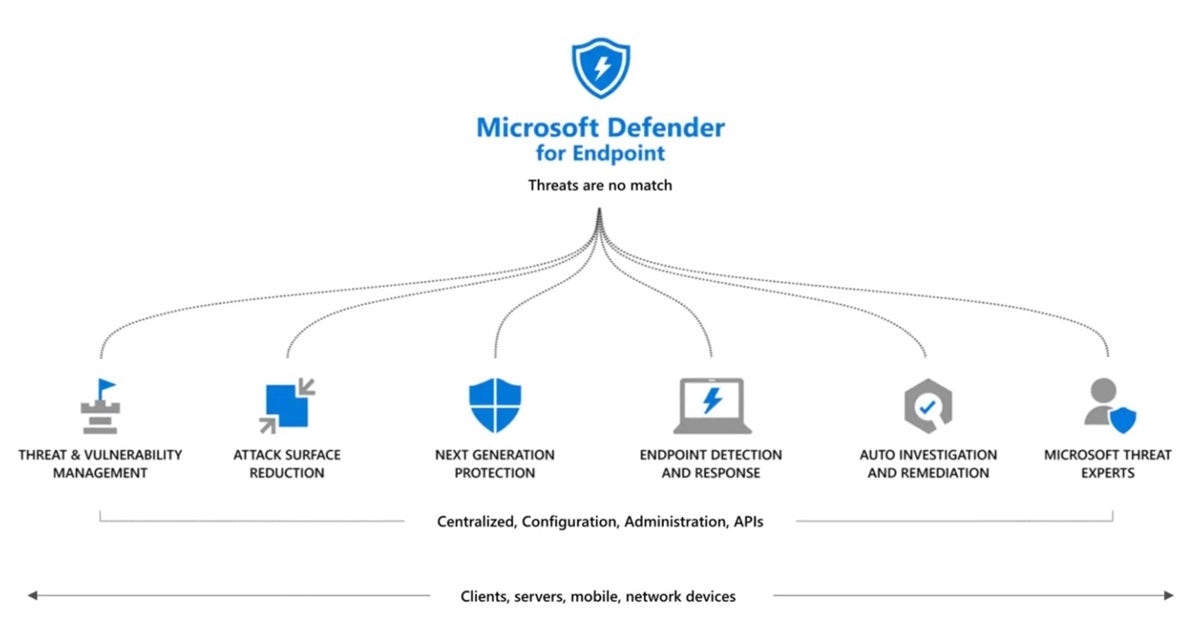
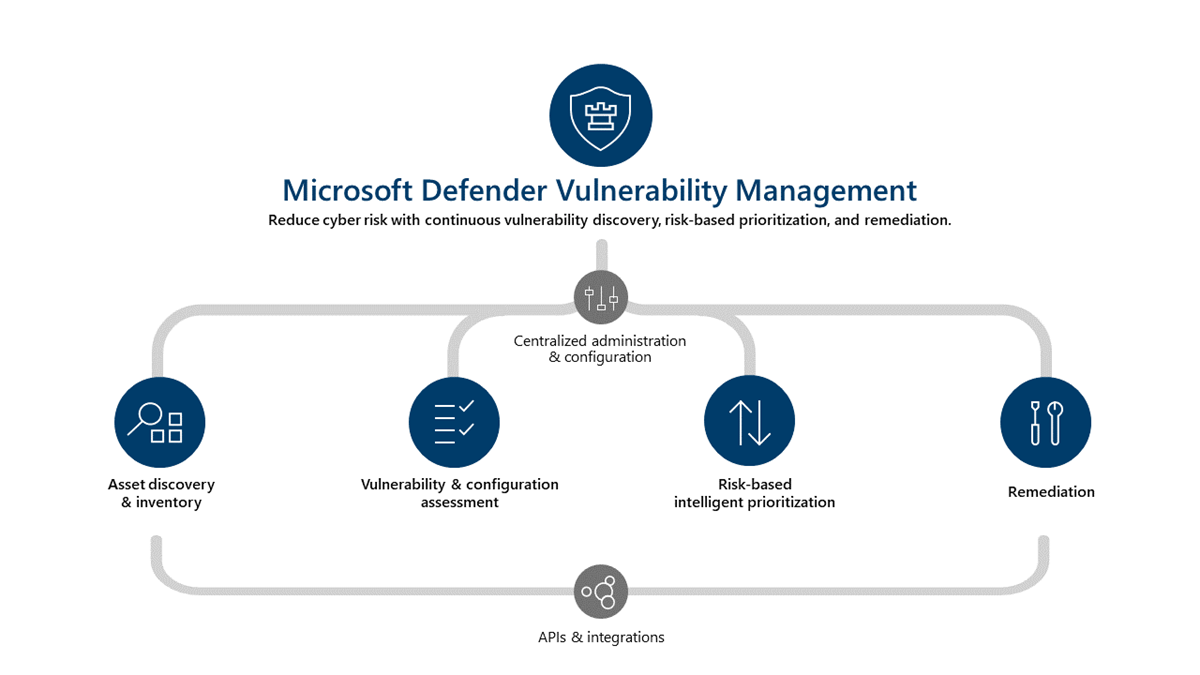
Security in Microsoft 365 – Exploring the Possible
We will walk you through the key pillars of Microsoft 365 and teach you on the different security features that are available per licensing type.
Security in Microsoft 365 – Exploring the Possible
We will walk you through the key pillars of Microsoft 365 and teach you on the different security features that are available per licensing type.